Quantum Tokens
A New Frontier for Secure
Transactions
Unforgeable transactions with
local validation and redemption
privacy, powered by quantum

What’s NewNews
World's First Successful Trial of Quantum Tokens Created Using Commercial Quantum Technology(mitsui.com)
White Paper : Quantum Tokens A New Frontier for Secure Transactions(quantunuum.com)
FeaturesMain Features of Quantum Tokens
Unconditional
Unforgeability
Thanks to the properties of quantum physics, malicious users are unable to double spend a token.

Local Validation
Quantum tokens can be validated locally without communicating with other systems. This speeds up the token redemption.

Redemption
Privacy
Much like with cash, the user only reveals the redemption branch when they redeem the token.
ConceptThe Future of Quantum Security
Quantum tokens combine quantum and classical technology to enhance security. Tokens are delivered using commercial QKD hardware, which ensures they cannot double spent. However, they are then converted into digital data, to allow them to be easily stored and redeemed later. Validation is performed locally, thanks to the special properties of tokens which accelerate the token redemption.
How it WorksThe Mechanism Behind Quantum Tokens
Issuance and Verification via Quantum Communication
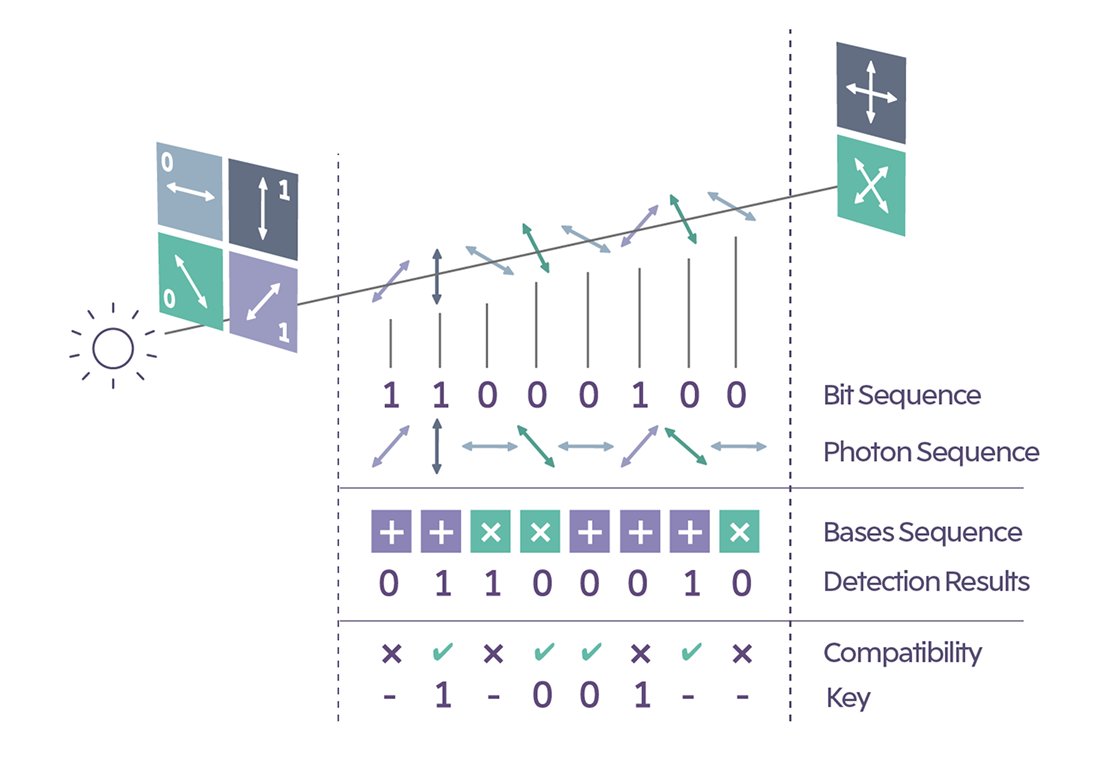
Quantum tokens are a new security technology based on quantum communication. By using non-orthogonal quantum states, they exploit the no-cloning theorem and classical methods to prevent forgery and double-spending.
In this scheme, the Issuer selects quantum states randomly from two conjugate bases and sends them to the Receiver, who measures the states and stores the outcomes. Later, these outcomes are checked against the Issuer’s secret information (which states were originally sent), allowing the token’s validity to be verified.
A representative implementation of such quantum communication is the BB84 protocol, originally proposed for quantum key distribution (QKD). Thanks to its extensive theoretical and experimental record, it has also been applied in the demonstration of quantum tokens.
Distribution and Usage via Secure Classical Communication
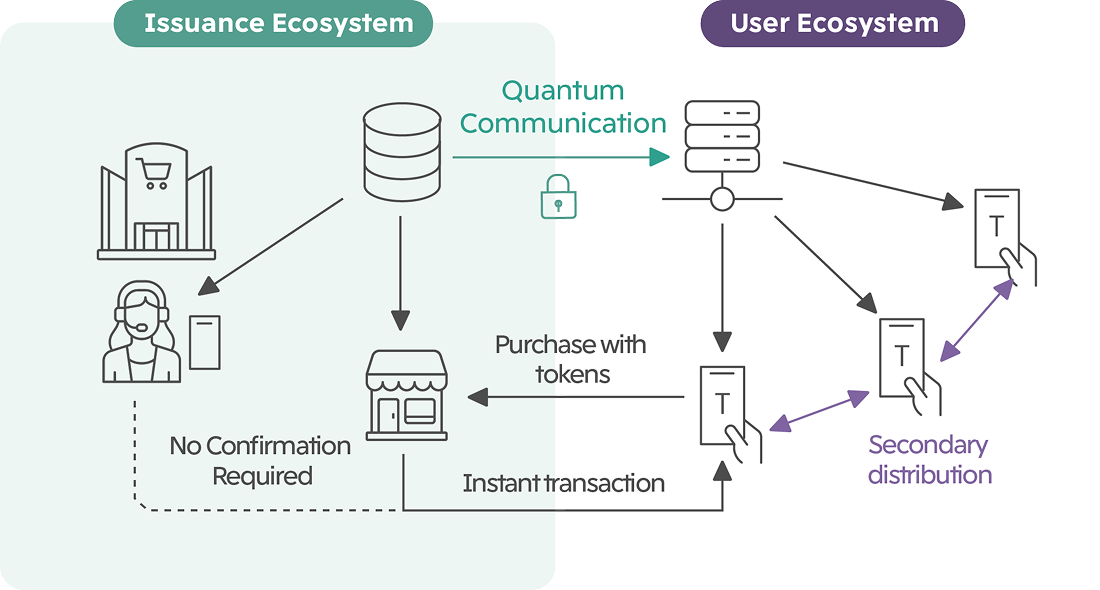
The Receiver transfers the measurement outcomes to a single Token Holder, who then becomes the legitimate owner of the token. The Token Holder can present the outcomes to merchants or service providers for use, and where it is validated locally. The Token Holder can also transfer (reassign) the measurement outcomes securely to another user via classical communication.
This design means that while quantum communication between the Issuer and Receiver is subject to distance limitations, actual users can use quantum tokens anytime and anywhere, including in online shopping.
Furthermore, the secondary distribution of tokens can be recorded on blockchains, transparency logs, or decentralized identifiers (DIDs), ensuring both transparency and security.
Use CasesUse Cases of Quantum Tokens
 Colocation-based high-frequency trading
Colocation-based high-frequency trading
Quantum tokens streamline high-frequency trading by synchronizing a user’s total order volume and trading conditions across colocations near exchanges. When a token is presented at a chosen colocation, the local algorithm executes trades based on market conditions while keeping the execution site secret until the moment of use, preventing front-running and manipulation. Thanks to the properties of quantum tokens, the total order does not need to be split across colocations, ensuring consistent management across regions. Local validation enables immediate order activation.
 Commodity-backed tokens
Commodity-backed tokens
Commodity-backed tokens are digital representations of tangible assets, such as precious metals or foreign currencies. These tokens are issued by a central authority at the risk that a malicious user exploits the token more than once. To avoid such double spending, quantum tokens offer an unforgeable solution to trade with tangible assets, securing their fair use and providing peace of mind to the central authority. Users can also benefit from the redemption privacy and local validation of quantum tokens whenever they exchange them for value.
 IoT Authentification
IoT Authentification
IoT devices often require real-time operation and must function quickly and reliably. Authentication through the cloud or remote servers in device-to-device communication can introduce delays and security risks. By using quantum tokens, devices are authenticated locally without relying on external networks, allowing them to operate autonomously. This results in a fast, stable IoT network, minimizing the risks of data leaks or malicious external interference.
Collaborate with
Us in Early-Stage
Research
Contact Us About Quantum Tokens
PartnersStrategic Partners
Quantinuum is the world leader in quantum computing. The company’s quantum systems deliver the highest performance across all industry benchmarks. Quantinuum’s over 550 employees, including 370+ scientists and engineers, across the US, UK, Germany, and Japan, are driving the quantum computing revolution. For more information, visit https://www.quantinuum.com
